I recently read an article by Michael Gale about digital transformation.
His book about the digital helix is pretty interesting too.
My immediate question was: is there a digital helix zone for cybersecurity?
The answer: Well of course!
Looking at the different aspects of what companies face when addressing the topic of cybersecurity, it is easy to come up with a similar picture.
Cybersecurity Drivers
We have strong and very complex drivers in cybersecurity. Regulations like PCI DSS, GDPR, CCPA and others force organizations to implement security technology and protect data. And while there are new regulations coming up from time to time, there are also internal audits and requirements of partner organizations that force companies to act. While the shared goal of these regulations is to protect consumers’ privacy rights or the assets of partners, they all differ in certain ways and cross-regulatory compliance can become an issue.
In addition, there is the risk of getting breached, which can result in loss of market share and customer trust. Then there’s the risk of ransomware that can cost millions when it comes to fallback and the risk of competitors getting access to company secrets and sensitive data.
Other companies try to monetize data and use modern technology like the cloud or hybrid infrastructure. Sharing sensitive data with an analytics platform or uploading it to the cloud requires strong cybersecurity and data protection, which can be a driver in itself.
These drivers need to be well understood to make sure there is an ROI when it comes to cybersecurity spending.
Cybersecurity Challenges
The same is true for challenges. Companies need to understand the market, the available technology, and the need to invest in people.
- Talent Acquisition – there’s high demand for cybersecurity talent in the market. Companies are investing a lot to find experts to implement sophisticated cybersecurity plans.
- Network Complexity – modern networks are becoming increasingly complex, which results in gaps and vulnerabilities, making it even more difficult to protect those networks from threats.
- The Burden of Choice - with the increasing amount of vendors and technology available, security leaders struggle to identify the right solution. Often there is more than one solution available to solve a specific problem, which results in seemingly endless opportunities and vendors trying to convince you that they hold the one and only solution.
- The Human Element - company culture is another big challenge when it comes to cybersecurity. While a lot of problems can be solved with technology, user error can still be a major security issue.
Only by accepting and acting on these challenges are companies able to implement and invest in the right solutions.
Cybersecurity Investments
Companies need to get the right budget for cybersecurity.
While CISOs, cybersecurity leaders, and data protection officers are connected to the board more and more, there is still a long way to go. Education is needed to free up budget to secure a company’s growth.
And there are two things companies need to understand:
- Having a big budget doesn’t solve any problems until you know HOW to invest it and how to measure success, which is a challenge in itself when it comes to cybersecurity
- Even when you have the budget to invest in EVERY security solution the market has to offer, there will NEVER be 100% security
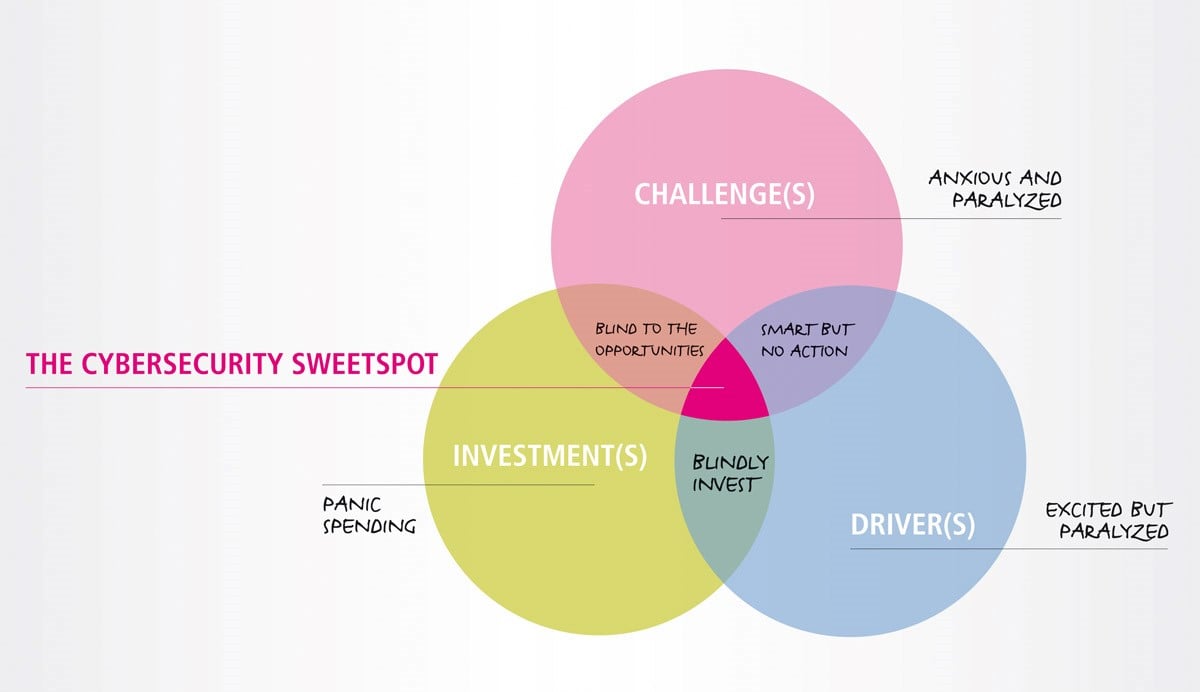
The Cybersecurity Sweet Spot
Let’s come back to the Venn diagram in the title picture. We adapted Gale’s Digital Helix Zone a bit to fit to the cybersecurity world. But it is very interesting:
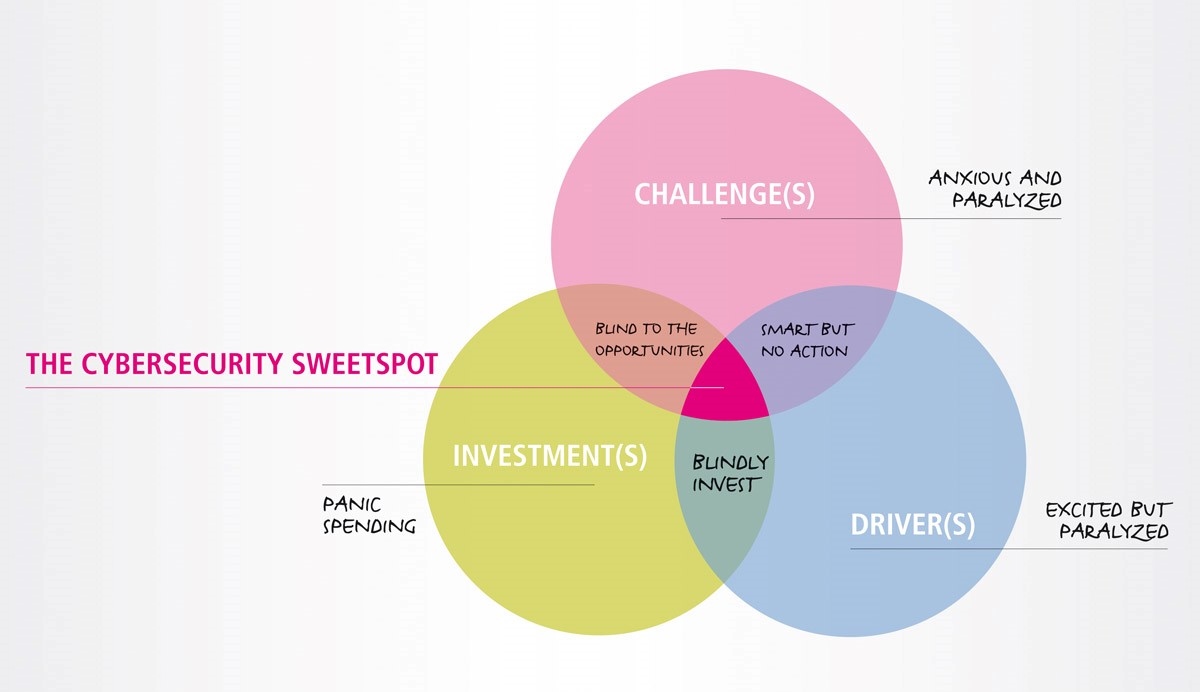
Anxious and paralyzed: While it seems weird that companies would have a good understanding of the challenges they face but wouldn't understand the drivers of cybersecurity, nor have sufficient funds dedicated to it, this is not an uncommon situation. An ill-informed board can misinterpret market drivers and therefore end up skimping on budget. This often occurs when compliance is misunderstood or simply underestimated and insufficient funds are allocated to it so the company can invest more in growth, rather than security.
Organizations that do this are at high risk.
Smart but no action: This means understanding the drivers and knowing what to do but not having the right budget available. Oftentimes it's less about money and more a question of communication and priorities. Wherever security is seen as a burden rather than an enabler, companies tend to postpone important investments – favoring investments with more immediate ROI.
Excited but paralyzed: Some companies see the need to implement cybersecurity, but when budget and an understanding of the challenges are missing, those companies are paralyzed; unable to change their situation.
Blindly investing: While some companies understand the need to act and have budget available, they are blindly investing in security solutions that don’t fit their needs, because of missing expertise in their company or missing knowledge of their infrastructure and company culture.
Panic spending: While some organizations understand that there is a need to invest in cybersecurity, they are unaware of the drivers and don’t have the knowledge available to make the right decisions. As Michael Gale stated: “these companies tended to over-invest in IT, consulting services and the idea of the day.” The same is true for cybersecurity investments.
Blind to the opportunities: Other companies have the right cybersecurity knowledge available and they get the budget. While this is usually great news, there are two risks. If not aligned with market drivers, there is the risk of a low ROI when implementing a great solution that doesn’t fit your needs. The best security solution is worth nothing if it doesn’t solve a real problem. Those organizations usually have high expectations but aren’t able to measure success.
The Cybersecurity Sweet Spot: Where cybersecurity, risk management and the board are well connected and communication is working, there are no silos anymore. Those companies solve the right problem, with the right solution, spending the right amount of money. The risk department of the company understands the drivers, the cybersecurity department is well aware of the solutions available and reacts with an actionable plan and the board is well educated, informed, and frees up the required budget.
Conclusion
So what can we learn from this Venn diagram?
Essentially, there is the sweet spot that we all want to live in. And this requires good communication and knowledge of both the market and technology. While knowledge is something you can buy, communication is far more important. This is especially true when it comes to cybersecurity, which is a topic that is as broad as could be. It spreads over the entire company and reaches from the firewall to the mindset of each and every employee.
And it’s an ongoing project. Being in the sweet spot today doesn’t mean you’ll be in the sweet spot tomorrow. Cybersecurity decision makers have to constantly work on knowledge, understanding of market drivers, and educating the board.
This is only possible with the help of trusted partners.
About comforte
So, what should a vendor like comforte tell you now?
That we have the perfect solution that'll solve all your problems?
Sorry. That'd be nice but the truth is there is no silver bullet when it comes to cybersecurity. And in the complex world we live in, there is no black and white.
But we strongly believe that many companies struggle with cybersecurity and are still investing in technology that tries to prevent breaches when what they should be doing instead is protecting the data itself.
Give us a shout and let us evaluate if we are able to help you protecting your data. That’s what we love to do.