In recent years we have been observing a greater and more rapid adoption by countries of data protection laws that try to combine security with technological and economic innovation. The emergence of new technologies that generate, store and use data, such as artificial intelligence, advanced analytics, cloud computing, the internet of things, among many others, has led governments to legislate how information is collected, stored, used and transferred.
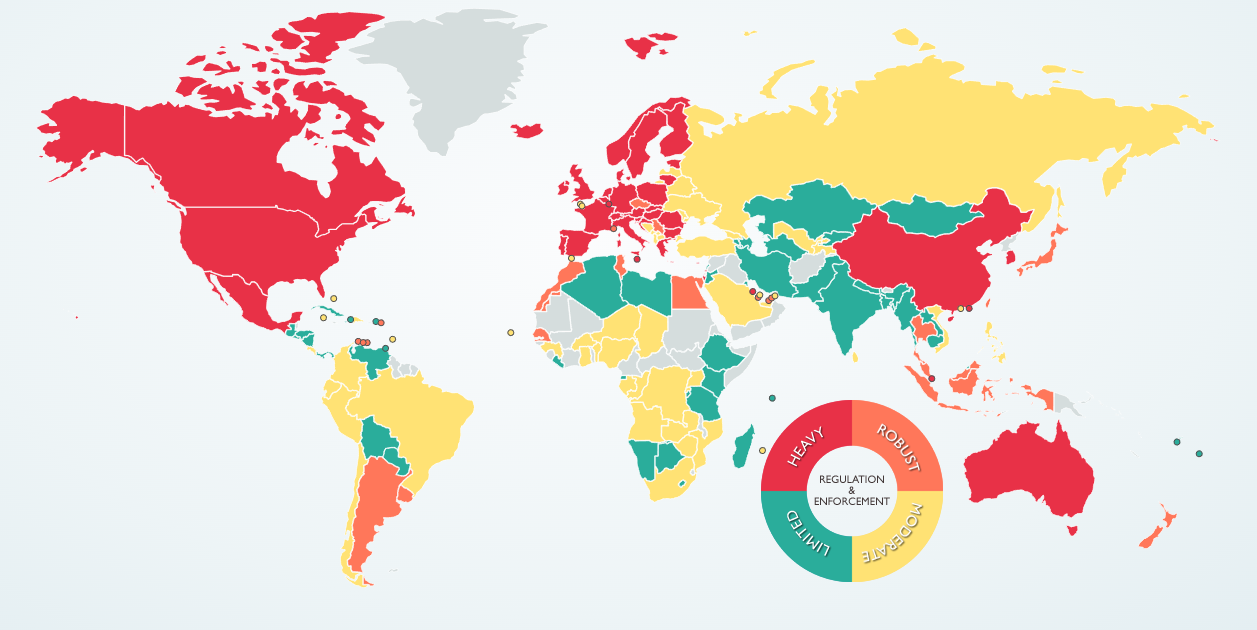
Data Protection Laws around the world - Source: © 2023 DLA Piper
Under this data legislation, appears a new term called Data Sovereignty: this is a legal concept about regulatory compliance in information management. It is closely linked to data protection, Cloud, and technological sovereignty. The objective is to answer the following questions:
- Who is the owner of the data?
- Who can and how should the data be stored?
- How can data be protected?
- Who can use them?
Specifically, talking about Data Sovereignty is to take into account three aspects of data management: infrastructure, administration and operation, and uses of data.
What is Data Sovereignty?
Data Sovereignty refers to the set of obligations and rights established by a series of conventions, rules and laws on the ownership, access, processing and storage of personal data. These regulations represent a guarantee of protection to users in order to prevent that data from being corrupted or compromised, ensuring that they are only accessible for authorized purposes and that they can be restored in case they become unusable or inaccessible. And, like all regulations, it has a geographical scope. For example, in a specific country or in an area such as the European Union.
An important issue to take into account about the sovereignty of data, especially with cloud storage, where database servers may be located in different countries, is to know and understand what regulations govern the information we have stored.
Another relevant aspect in the use of cloud services and the use of external servers is to know and be clear about who owns the stored data. In order to guarantee the security of the data we have to make sure that the definition of ownership is clear.
Data Sovereignty offers many benefits to both companies and users, but organizations face significant challenges in its implementation, due to market limitations and regulatory restrictions. In this case, there are two key challenges that must be faced:
- If the service provider does not host your solution (SaaS) in local data centers
This challenge appears when cloud service providers do not host Software as a Service (SaaS) in local data centers. The implications are notably related to regulatory compliance. In regions such as the Middle East and North Africa (MENA), where the presence of data centers may be limited, companies may face difficulties in complying with local regulations.
To illustrate this scenario, let's consider a company with operations in the MENA that depends on a SaaS provider whose data centers are located in another region. The geographical distance can result in greater latencies, affecting operational efficiency and the end user experience. In addition, local regulatory restrictions can generate concerns about privacy, data security and data transfer. - If the availability of cloud solutions is limited due to concerns or restrictions about the location of the data
In this case, it highlights the specific limitations faced by organizations in terms of cloud solutions. Let's imagine a company subject to the General Data Protection Regulation (GDPR) operating in the European Union. Concerns about data residency may restrict your choice of cloud service providers that ensure regulatory compliance.
In this context, the company may be limited in its ability to adopt cloud solutions that provide specific functionalities due to geographical restrictions. This not only affects business agility and competitiveness but also highlights the need for careful consideration of the location of data when selecting cloud service providers.
Companies and the Cloud?
The implications of data sovereignty for companies that are digitized companies or are in the process of digitization, is that they must pay attention to two basic rules to guarantee the security of the data:
- IT infrastructure must always be secure, flexible and modern (up-to-date): Companies must invest in infrastructures that not only meet current security requirements, but are also adaptable to future technological evolution. Keeping up to date is essential to address constantly changing threats.
- The sovereignty and security of the data of customers, users, and companies must be guaranteed: When choosing cloud service providers, companies must ensure that they clearly understand where the data is stored and how it is protected. Data sovereignty regulations vary by region, so it is vital for companies to align their practices with local laws.
With data protection precautions and the corresponding contractual rules, companies will be able to protect and process data in compliance with data protection laws.
A key point is to clearly understand how cloud service providers treat data and what rights the company has.
What should be taken into account for data protection?
Companies that process personal data must take into account the legislation in force in the country. With regard to GDPR, it is emphasized that companies apply the appropriate technical and organizational measures to guarantee the level of security appropriate to the risk.
The essential technical and organizational measures that companies must take into account are:
- Tokenization (anonymization) of data: Tokenization is an effective approach to preserving privacy by replacing sensitive data with tokens. This ensures that even in case of unauthorized access, the data is unintelligible without the corresponding token.
- Confidentiality and integrity of the system: Ensuring confidentiality implies the use of encryption and network security techniques. In addition, the integrity of the system is maintained through security protocols that protect against unauthorized data modifications, once again, tokenization can help protect data.
- Technical resilience of systems: Resilience implies the ability to recover quickly from adverse events. In the context of data protection, this involves the implementation of regular backups and the ability to restore data in case of loss.
- Restoration and availability of data after technical failures: Disaster recovery plans are essential to ensure the continuous availability of data. This involves not only the restoration of data, but also the rapid resolution of technical problems.
- Periodic check, evaluation and evaluation of security measures: Data security is a continuous process. Companies must carry out regular audits and evaluations to ensure that their security measures are effective and conform to changing threats.
- Compliance with and incorporation of data protection measures by employees: Training and awareness of employees are vital. Companies must ensure that employees understand and comply with data protection policies, since they are often the first line of defense against internal threats.
There are several solutions to achieve data sovereignty, on the one hand to have a cloud provider that is subject to the same regulatory and legislative framework as the country of residence of the company.
Another alternative is the one based on Multicloud, where we would have the distribution of data in different clouds and regions, the answer would be to apply a customized governance and compliance policy for the most sensitive information, that is, that this sensitive information is under the same legal framework in which the company is.
And finally there is an alternative, which also protects even more and increases security also in the two previous solutions, which is to incorporate additional information protection measures into our systems.Specfically, we are referring to technologies that protect data with anonymization from origin such as tokenization. This serves to guarantee the confidentiality and integration of the data, and that the data would only be available to the owner of the data.
What additional considerations should be taken into account in a Multi-Cloud and Multi-region strategy?
As we have mentioned before, organizations face significant challenges in their implementation for compliance with Data Sovereignty, especially in regions where the infrastructure of cloud services may not be as developed as elsewhere. The absence of local suppliers or the limited presence of data centers in certain areas can create obstacles to advance in competitiveness, efficiency and innovation and at the same time with the obligation to comply with data protection laws.
Let's imagine a company with operations in the Middle East and North Africa (MENA), where the availability of cloud services can be limited. In this scenario, the Multicloud strategy becomes a strategic and necessary response. It allows organizations to overcome geographical limitations, optimizing operational efficiency and ensuring regulatory compliance.
To do this, they must take into account the following recommendations to overcome this limitation:
- Governance Policies: In regions where the presence of data centers may be scarce, implementing specific governance and compliance policies becomes crucial. These policies ensure that the data is aligned with local regulations, while allowing an agile adaptation to changing regulatory requirements.
- Selection of Providers: The choice of cloud service providers becomes a vital element of the Multicloud strategy. By selecting suppliers that meet local regulatory requirements, companies can overcome the lack of local infrastructure and guarantee data security.
- Data Location: The distribution of data in different clouds and regions is not only a strategy to comply with the laws, but also a way to circumvent geographical limitations. Understanding and adapting to local regulations becomes an essential component of this strategy.
- Contractual Agreements and Continuous Monitoring: Establishing clear contractual agreements with suppliers and performing periodic evaluations becomes even more critical in environments where local infrastructure is limited. These contracts must address data protection, security and regulatory compliance in all relevant locations.
The Multicloud strategy becomes a fundamental enabler for business agility and innovation and compliance with data sovereignty regulations in regions where cloud service infrastructure can be a challenge.
Conclusion: Ensuring Data Protection and Data Sovereignty Compliance
In summary, implementing additional information protection measures not only strengthens data security, but also plays a fundamental role in complying with the principles of Data Sovereignty. These measures, such as tokenization from the source, not only preserve privacy by replacing sensitive data with tokens, but also ensure that, even in situations of unauthorized access, the data remains unreadable without the corresponding token.
This approach not only contributes to the confidentiality and integrity of the data, but also guarantees that the data is only available to the legitimate owner. By adopting advanced data protection technologies, companies not only comply with local data protection laws, but also reinforce their position in the secure management of information in a globalized environment.
By choosing between alternatives such as cloud service providers subject to the same regulatory framework as the country of residence or Multicloud-based strategies, where a customized governance and compliance policy is applied for the most sensitive information, companies not only optimize operational efficiency, but also reinforce the protection and sovereignty of their data.
Ultimately, the combination of good security practices, the detailed understanding of local regulations and the implementation of advanced technologies become the solid basis for a comprehensive Data Sovereignty strategy that protects data, guarantees regulatory compliance and strengthens the company's position in an increasingly interconnected world.






