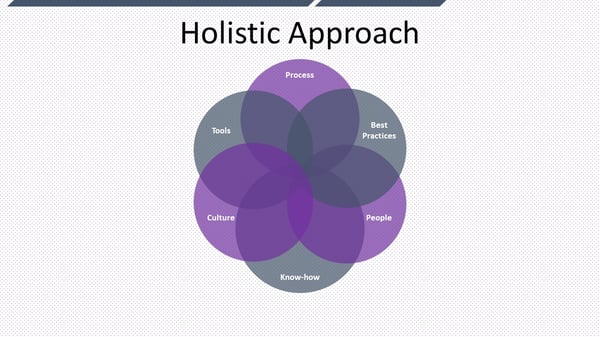
Holistic security means more than just implementing one tool, one method, one solution, or one process to protect your business’s data. It means exploring every avenue to implement a multi-pronged defensive strategy and never depending on just a single security tool or solution. Organizations that follow more holistic approaches to security are the ones best positioned to remain in compliance with internal and regulatory mandates and to prevent breaches or unauthorized access of sensitive data. They’re the ones who can best protect their intellectual property, their brand reputation, and their customers’ most sensitive data. Let’s dig in a little bit to figure out how you can be more holistic in the way you view security within your organization.
Even today, with the nearly non-stop drumbeat of news about corporations whose most sensitive information has been compromised, stolen, or taken hostage, most vendors will still tackle security from one angle only (like implementing a good firewall or intrusion detection solution, or focusing on better password creation and protection among users), which is the complete opposite of a holistic stance. This narrow, single-sided approach is no doubt at least a contributing factor to the growing frequency of cyberattacks on and data breaches within enterprises both small and large. Modern cybersecurity is more than just having the latest and strongest perimeter security mechanism in place, as this alone is going to be largely ineffective when you consider that given enough time and patience, a threat actor can penetrate any perimeter (not to mention bad actors on the inside who might already be working surreptitiously toward nefarious ends). A holistic stance encompasses multiple or even many critical tools/technologies, starting with those to protect the perimeter but going well beyond that to protecting the data itself wherever it happens to be: behind the perimeter at rest, or data in motion within or even outside the perimeter.
Holistic security goes beyond defensive tools themselves. It means assessing the data-handling processes and information workflows that your workers carry out within your organization, such as where and when they create, handle, share, store, and transmit data, and how to protect that data both at rest and in motion. By the way, being holistic isn’t just for large global companies with tons of users and associated resources to support them. Even a two-person business generates an enormous amount of information, and some or even a lot of it is no doubt quite sensitive (customer data including payment information, intellectual property, competitive information). If a small company generates or houses this much sensitive data, then go ahead and think of how much sensitive data resides within large enterprises. To be holistic, you need to focus on the best practices and controlled processes to protect data at its earliest possible moment and never de-protecting it if at all possible, without actually interfering with the work that needs to get done with that data. Everybody in the organization has to be security-minded, and the processes need to be quite clear and easy for them to follow as they work with your company’s data.
Human factor
You can probably see that this holistic approach to security that I’m talking about involves accounting for the human factor not only in terms of threat actors (how they think and behave, what they’re really after, and how they’re going to try to get to it) but also in terms of the employees and how they view, work with, and treat information. Business and security leaders must evaluate the corporate culture itself within the organization. How do users and employees evaluate information that they process and handle? How do they make decisions related to data security? What type of information is public for general consumption versus private and confidential? Will two people always make the same objective decision regarding security classification in the same situation?
Well, probably not actually. For example, two employees who may have had the same standard information security training but who operate in different departments (let’s say Sales and R&D) might actually view certain information very differently, at least insofar as the appropriate uses and treatment of that data. One may deem it highly sensitive and well worth protecting vigorously, while the other may not necessarily see just how sensitive the data really is and therefore not protect it as much. No matter how well guarded the perimeter is, defensive tools can’t necessarily prevent inadvertent breaches or exposure of sensitive information due to data mishandling. Therefore, establishing a comprehensive company-wide policy for data processing and data handling and then constantly monitoring the effectiveness of that security-minded culture is an essential component of developing an overall holistic security posture.
Your business’s security is only as good as your workforce’s dedication to bolstering and strengthening the security-mindedness of the organization as a whole; no single tool can replace the effectiveness of a security-conscious workforce. Therefore, it’s the responsibility of the whole company to ensure that everyone is on the same page when it comes to data security and not down to a select few, such as the CISO and her staff, or those folks over in IT whose job it is to run the IT infrastructure. You need more than cutting-edge security tools, though these are certainly a necessity. You need policies and processes that your employees understand and that everybody can put into action. What you don’t need is for your knowledge workers to feel that security is “somebody else’s problem, not mine.” Being holistic means putting in place the right controls to complement your data security tools and solutions.
It's a concert
So, hopefully I am being clear: it’s not just about the tools, it’s not just about the processes, and it’s not just about the corporate best practices you implement across your organization—it’s about all of them at once working in concert along a multi-dimensional security strategy that is flexible and adaptive.
Lots of resources are out there to help you begin thinking about a holistic security framework. The Center for Internet Security (CIS) is a great place to start—their CIS Controls framework lays out prioritized actions you can take to better protect your business from attack. If your business already has a strong cloud initiative (and of course, it should!), why not check out the Cloud Security Alliance? This site is the place where you can learn about the CSA Cloud Controls Matrix (CCM), which will help you with assessing security controls for cloud technologies and infrastructures.
Complacency can be risky
All of this is to say that a company adopting that best-case-scenario holistic stance to security will be mindful of all these aspects and controls, and not just direct attention and effort to one part of the equation only. Cybercriminals never stop and they always consider every single angle no matter how minute, so your security posture must be at least as comprehensive if not more so. Complacency is a dangerous habit that must be removed from the equation through this holistic approach to data security. Having a complete view of the cyber-environment will enable organizations to better tackle today’s multifaced cyber-threats.
Photo Credit: freepik.com






