There’s a world of difference between retail and private banking. While the former is transactional and focused on the mass market, the latter is...
Jan 15, 2026 l Data Protection, Business Value
Delivering a Secure, Trusted Foundation for Cloud Growth at LGT
Dec 11, 2025 l TAMUNIO, Data Security Platform
Looking Back at a Year of Mounting Risk but New Opportunities
It’s been another 12 months of high drama and escalating threats. For cybersecurity leaders managing risk in some of the world’s largest and most...
Data breach costs surged by 9% annually to reach $10.2m in the US over the past year. But among the most sure-fire ways to reduce those costs are...
Oct 23, 2025 l TAMUNIO, Data Security Platform
Turning Data Security from a Cost Center into a Growth Enabler with TAMUNIO
The security function has often been at odds with the rest of the business. While the latter guns for growth, CISOs have historically been seen as...
Oct 16, 2025 l TAMUNIO, Data Security Platform
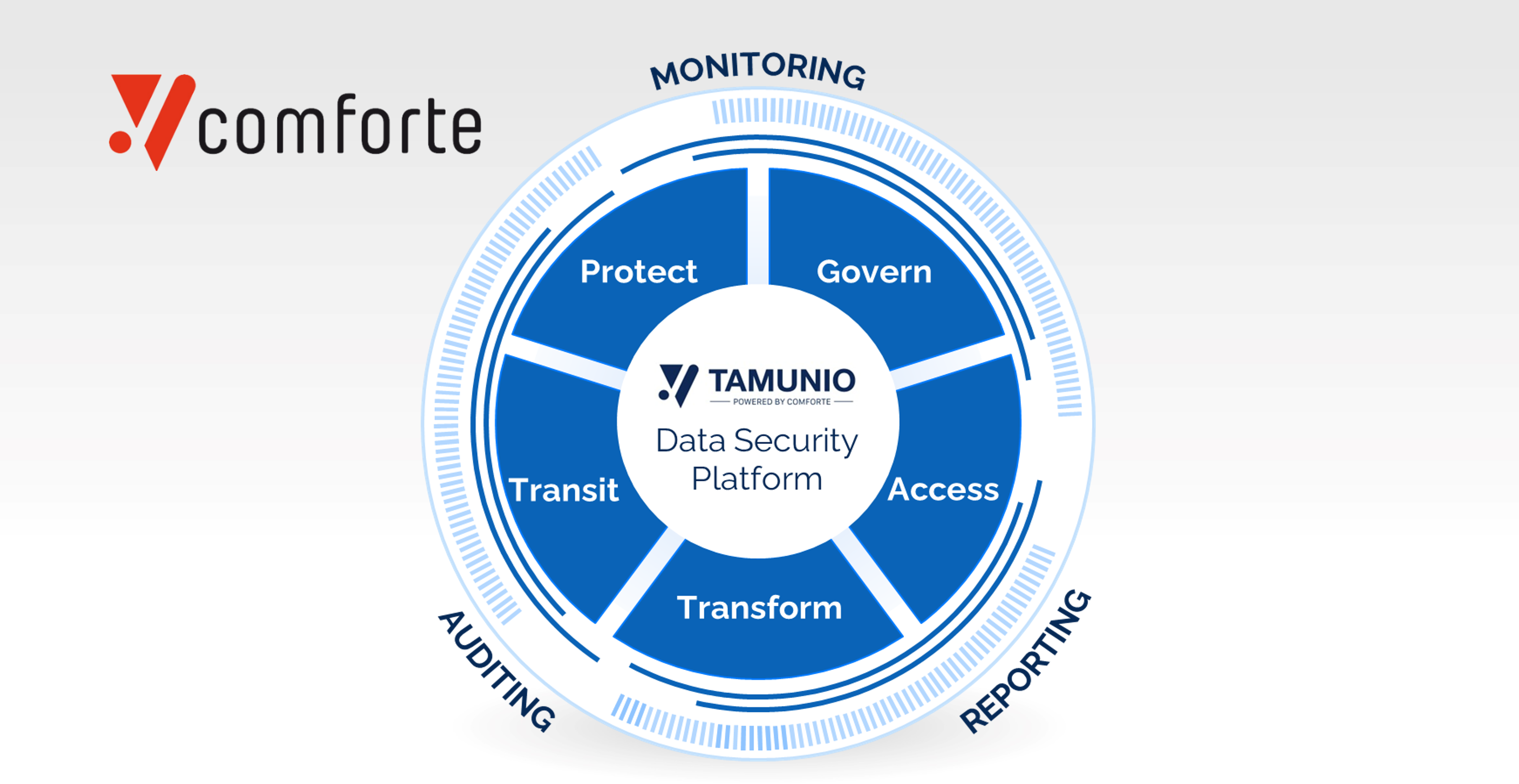
Introducing TAMUNIO: Why It’s Time for a New Approach to Data Security
Today’s enterprises are caught in a modern version of the Innovator’s Dilemma. On one side, the demands of security and compliance are intensifying,...
Jul 24, 2025 l PCI DSS, Compliance
How Vaultless Tokenization Works in Practice, to Transform Your Business
In last month’s blog post we explained how vaultless tokenization can transform PCI DSS 4.0 compliance from a regulatory burden into a business...
Jun 26, 2025 l PCI DSS, Compliance
Is PCI DSS 4.0 Slowing You Down? Here’s How comforte Can Accelerate Your PCI Compliance Journey
With the latest version of PCI DSS, the Payment Card Industry Security Standards Council (PCI SSC) aims to elevate the standards for cardholder data...
May 22, 2025 l Data Protection, Digital Enablement
Top Indicators You Have a Cybersecurity Problem—and What to Do About It
Data is both blessing and curse to the modern enterprise. Yes, when analyzed effectively it can surface intelligence to improve decision making,...
May 15, 2025 l Data Protection, Compliance
Streamlining PCI DSS 4.0 Compliance for IBM Z Series Customers
IBM Z Series customers traditionally include some of the world’s biggest financial services and retail companies. This puts them firmly in the...