There is a basic question we want to answer in this series: Is it really true that “compliance isn’t security”?
We started with lessons from the past and looked at the fight of regulations against cybercrime. We saw that regulations have evolved and become better and better – but so has hacking. So now let’s take a look at how we got here.
Part I: Lessons from the Past
Part III: What's Next?
The origins of hacking – the good old days & how hacking has evolved
Hacking has always been there - since the beginning of information technology there have been those trying to disrupt it. In the early days, most hackers were just breaking stuff for fun.
It all started in 1903 when Nevil Maskelyne, a magician and inventor, interrupted a presentation of a wireless telegraph by sending insulting Morse code messages. Just a few decades later, Alan Touring was brute-forcing Germany's enigma machine for military purposes in 1939 and in the late 40s, John von Neumann described the theory of self-reproducing computer programs, what we refer to today as viruses.
From the 50s to the 70s, hacking was mostly reserved to local systems and individual penetration.
By 1981, the New York Times described hackers as: “technical experts; skilled, often young, computer programmers, who almost whimsically probe the defenses of a computer system, searching out the limits and the possibilities of the machine. Despite their seemingly subversive role, hackers are a recognized asset in the computer industry, often highly prized”.
After an increasing number of break-ins into corporate and government computers, the US Congress passed the Computer Fraud and Abuse Act, which finally made it a crime to break into systems in 1986.
But hacking didn’t stop. And even with all the regulations in place and all the security technology available - the impact of breaches has grown significantly since the 80s, and it’s still growing – here are a few examples:
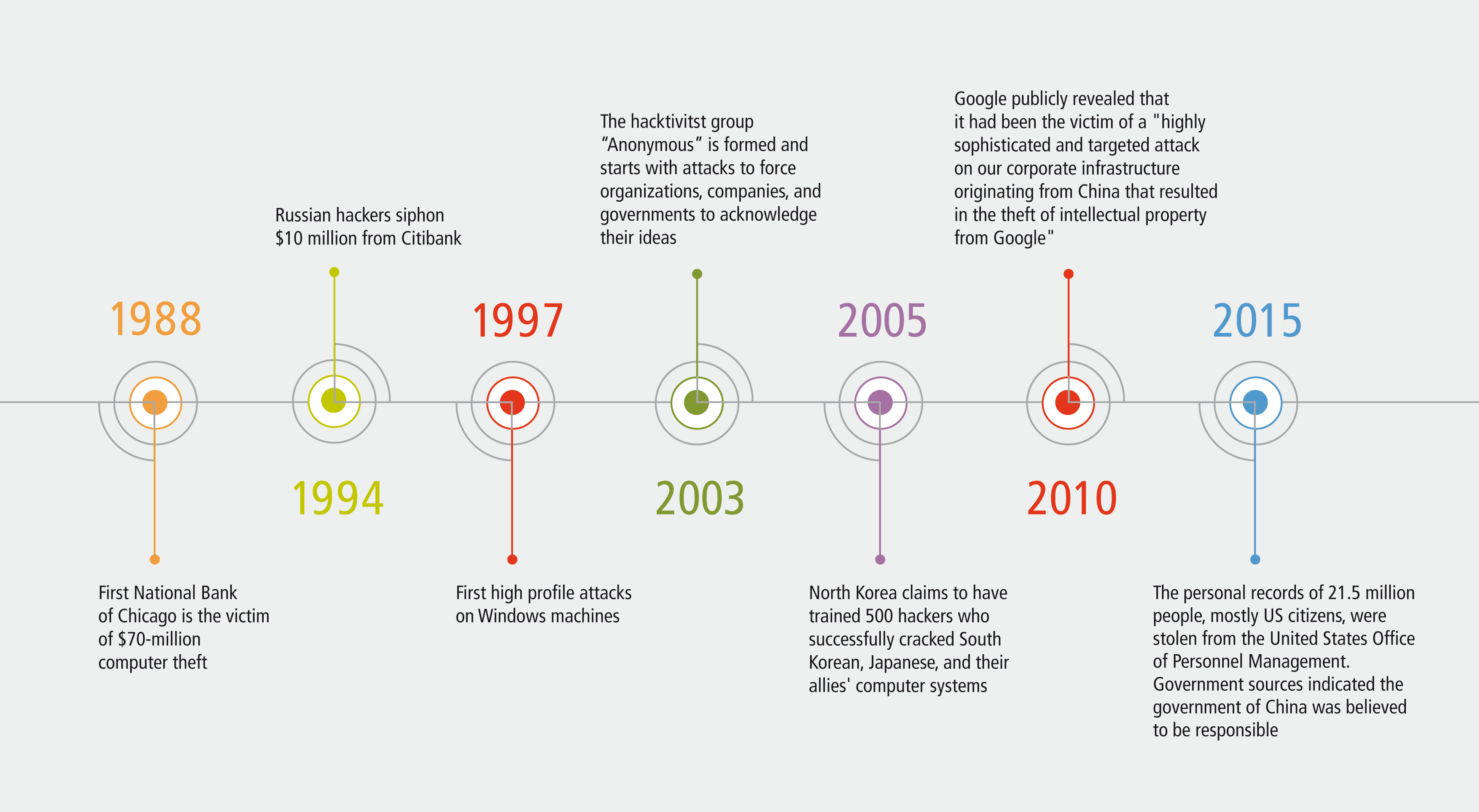
- In 1988 the First National bank of Chicago was the victim of $70-million computer theft
- In 1994 Russian hackers siphoned $10 million from Citibank
- In 1997 we had the first high profile attacks on Windows machines
- In 2003 the hacktivitst group Anonymous was formed and started with attacks to force organizations, companies, and governments to acknowledge their ideas
- In 2005: North Korea claimed to have trained 500 hackers who successfully cracked South Korean, Japanese, and their allies' computer systems
- In 2010 Google publicly revealed that it had been the victim of a "highly sophisticated and targeted attack on our corporate infrastructure originating from China that resulted in the theft of intellectual property from Google"
- In 2015 the records of 21.5 million people, mostly US citizens, including dates of birth, addresses, fingerprints, and social security numbers, were stolen from the United States Office of Personnel Management. Press reports indicated that government sources believed the government of China was responsible for the attacks.
This is by no means a comprehensive timeline of every data breach from 1988 until 2015. These are just a few select examples to demonstrate how hacking has evolved over time and become increasingly sophisticated.
Cybercrime today – the balance of powers?
Over the last half century we went from obvious hackers, to criminal organizations stealing credit card information, and moved on to activists like Anonymous. Today, we have entered the age of cyber warfare. We’ve heard many examples of the West saying Russia, North Korea, or China are the sources of attacks.
And attacks are not only coming from the outside. Edward Snowden showed us that any thought of online privacy is an illusion. Governments are forcing organizations to hand over the private information of their costumers.
In reaction to cyber criminals, hacktivists, and foreign governments, organizations are scrambling to improve security. But how have attacks changed?
Types of attacks
New and dangerous types of hacks have emerged that have victimized government entities and prominent businesses like Microsoft, Sony, eBay, Yahoo!, Target, and Amazon. Most companies are shocked when they find out that the average time it takes to detect that a breach is 170 days.
Criminals are able to sell hacking as a service either directly by selling software or based in the cloud which has developed over last few years. The underground hacking industry and the legitimate industry are offering pretty similar services.
There are hacking services, there are escrow services, there are ransomware services and they're all very well organized. With $50-100 US you can rent a botnet to attack any website and put it down for hours or days.
In 2018 we are looking at machine learning and IoT – two things that don’t ease the situation. With memory based worms we have very specific malware now. If you have 15 computers attacked by these worms you might be able to recover, but there is no way to recover if you have an enterprise with a complex network and thousands of clients.
While Microsoft pays up to $100k US for discovering a Windows vulnerability or a zero day exploit, criminal organizations pay up to three times that amount. Unethical hackers turn around and sell it to the highest bidder, which leads to bugs and gaps that won’t be fixed for months or years.
What can we do about all of this?
The famous quote: “Know your enemy and know yourself, then you will not once be defeated in a hundred battles” doesn’t seem to be working here. In the end, it seems to be impossible to know your enemy at all. Hackers are always one step ahead.
But what can we do about it?
In the next post, we will look at the key takeaways and how to find the right data security strategy.


.jpeg)